Hai semuanya! Microsoft Defender for Endpoint, nih, solusi keamanan ujung tombak yang siap ngelindungi semua perangkat ente dari serangan siber yang nakal. Bayangin, semua ancaman langsung dideteksi dan ditangani dengan cepat, jadi ente bisa fokus ngerjain kerjaan tanpa was-was. Defender ini nggak cuma punya fitur keren, tapi juga gampang dipake, jadi siapa pun bisa ngatur dan ngawasin keamanannya.
Defender ini punya banyak banget komponen, mulai dari perlindungan real-time, pencegahan intrusi, sampai respon otomatis. Ada pula integrasi sama produk Microsoft lainnya, bikin keamanan makin solid. Dan yang paling penting, ada banyak pilihan deployment, cocok buat berbagai kebutuhan, mulai dari perusahaan kecil sampe yang besar banget.
Security Features and Capabilities
Microsoft Defender for Endpoint is a powerful security solution that protects your systems from a wide range of threats. It goes beyond simple antivirus, providing a comprehensive suite of real-time protection and automated response mechanisms. This comprehensive approach helps businesses proactively identify and mitigate security risks, safeguarding their valuable data and infrastructure.
Defender for Endpoint utilizes cutting-edge technologies to ensure robust security. Its multi-layered approach not only detects threats but also actively prevents them from causing damage. This proactive defense system ensures that your organization remains secure and operational.
Real-Time Threat Protection
Defender for Endpoint continuously monitors systems for suspicious activities in real time. This proactive approach allows for immediate detection and response to threats, preventing them from escalating into significant incidents. This real-time monitoring is crucial for maintaining a secure environment.
Intrusion Prevention System (IPS) Functionalities
Microsoft Defender for Endpoint’s IPS proactively identifies and blocks malicious activities. It does this by examining network traffic and system calls for known attack patterns. This prevents malicious software from executing and reduces the risk of exploitation. The IPS works in tandem with other security features to provide a comprehensive defense strategy.
Automated Response Mechanisms
Defender for Endpoint’s automated response capabilities are designed to quickly and effectively mitigate threats. When a threat is detected, the system can automatically take actions like quarantining infected files, blocking malicious connections, or even initiating remediation steps. This automated response helps minimize the impact of security breaches.
Security Intelligence Feeds
Defender for Endpoint leverages various security intelligence feeds to stay ahead of evolving threats. These feeds provide real-time threat information, enabling the solution to adapt to new and emerging attacks. These feeds constantly update the system’s knowledge base, allowing it to recognize and respond to sophisticated threats more effectively. Examples include feeds from reputable security research organizations, threat intelligence providers, and internal security data.
Integration with Other Microsoft Products
Defender for Endpoint seamlessly integrates with other Microsoft products, providing a unified security posture across your entire ecosystem. This integration enables a holistic security strategy, allowing you to leverage the combined strength of Microsoft’s security solutions. For instance, Defender for Endpoint can work in concert with Microsoft Intune to manage and secure devices remotely.
Threat Detection and Response
| Threat Type | Detection Method | Response |
|---|---|---|
| Malware | Signature-based detection, behavioral analysis, and file integrity monitoring | Quarantine or deletion of infected files, blocking malicious processes, and initiating remediation |
| Phishing | Email analysis, URL scanning, and user behavior monitoring | Blocking suspicious emails, flagging potentially malicious links, and educating users |
| Ransomware | File system monitoring, process analysis, and network traffic analysis | Immediate blocking of ransomware processes, restoration of encrypted files from backups, and remediation of vulnerabilities |
| Exploits | Vulnerability scanning, intrusion detection, and real-time threat intelligence | Patching vulnerabilities, blocking exploit attempts, and isolating compromised systems |
Management and Monitoring

Microsoft Defender for Endpoint empowers you to proactively manage and monitor your entire security posture. This comprehensive approach goes beyond just detecting threats; it enables you to understand the “why” behind security events, enabling rapid response and preventative measures. This streamlined process leads to a more efficient and effective security strategy, ultimately minimizing potential damage and downtime.
The intuitive interface allows for easy navigation and management of security policies and configurations, while detailed reporting and analytics provide valuable insights into potential vulnerabilities and security trends. You can configure alerts and notifications to suit your specific needs, ensuring that critical issues are addressed promptly. This allows you to proactively address potential threats and improve your overall security posture.
User Interface for Management and Monitoring
The Microsoft Defender for Endpoint user interface is designed for ease of use and efficient navigation. It provides a centralized dashboard for viewing key security metrics and actionable insights. A clean, well-organized layout makes it simple to monitor threats, manage devices, and configure security policies. This centralized approach allows for a holistic view of your security posture.
Reporting and Analytics Features
Microsoft Defender for Endpoint offers a rich set of reporting and analytics features. These features provide valuable insights into security events, enabling you to identify trends, patterns, and potential vulnerabilities. Detailed reports can be generated on various aspects of your security posture, including threat detections, device configurations, and policy compliance. This data-driven approach enables proactive security measures and reduces the risk of potential threats.
Configuring Alerts and Notifications
Customizable alert and notification settings allow you to tailor your security monitoring experience to your specific needs. You can configure alerts for various security events, including malware detections, suspicious activity, and policy violations. Notifications can be delivered through email, in-app alerts, or other designated channels. This ensures that critical security events are addressed promptly.
Dashboards for Visualizing Security Posture
Customizable dashboards provide a comprehensive overview of your security posture. These dashboards consolidate key metrics and security events, presenting them in a visual format. Key metrics like device health, threat detections, and compliance status are presented graphically, allowing for quick identification of potential vulnerabilities. This visualization provides a quick and easy way to understand the overall security posture of your organization.
Troubleshooting Common Issues
This section details troubleshooting steps for common issues encountered when using Microsoft Defender for Endpoint. Following these steps can resolve many problems quickly. Proper troubleshooting ensures your security solution is functioning optimally.
| Issue | Troubleshooting Steps |
|---|---|
| Agent not installed | Verify if the agent installation was attempted. If not, check the installation package and any prerequisites. Review any firewall rules or group policies that might prevent installation. If installation still fails, contact support. |
| High CPU usage | Check if any specific applications or processes are consuming high resources. Review logs to identify the root cause. Update or reinstall the agent. If the issue persists, contact support. |
| Connectivity issues | Verify network connectivity to the Microsoft Defender for Endpoint service. Ensure there are no firewalls or proxy settings blocking communication. Check the status of your internet connection. If connectivity issues persist, contact support. |
| Incorrect configuration | Review the configuration settings. Ensure that the configurations align with your organization’s security policies. Consult the Microsoft Defender for Endpoint documentation for appropriate settings. If the issue persists, contact support. |
Deployment and Integration
Getting Microsoft Defender for Endpoint up and running smoothly is crucial for maximizing its security benefits. This involves careful deployment planning and seamless integration with existing systems. Proper configuration ensures the solution works effectively across your entire environment, whether on-premises, in the cloud, or a hybrid model. Effective deployment and integration are key to securing your data and assets.
Deployment Methods
Various deployment methods are available for Microsoft Defender for Endpoint, catering to different organizational structures and IT environments. These methods include deploying via the Microsoft Endpoint Manager portal, utilizing the Defender for Endpoint agent, or leveraging the Defender for Endpoint API. Each approach offers distinct advantages and considerations that must be carefully evaluated.
Integration with Existing Infrastructure
Seamless integration with existing security infrastructure is essential for a holistic security strategy. Microsoft Defender for Endpoint can be integrated with security information and event management (SIEM) tools, allowing for centralized threat detection and response. Furthermore, it integrates with other Microsoft security solutions like Azure Active Directory, enabling unified identity and access management. Integration with existing security tools streamlines operations and enhances overall security posture.
Hybrid Cloud Deployment Guide
Deploying Microsoft Defender for Endpoint in a hybrid cloud environment requires a phased approach, considering both on-premises and cloud-based components. This guide provides a step-by-step process:
- Assessment and Planning: Evaluate your current infrastructure, identify vulnerabilities, and define specific security requirements for the hybrid environment. This includes defining the scope of the deployment, determining the necessary resources, and outlining the integration points with existing systems.
- On-premises Deployment: Deploy the Defender for Endpoint agent on all relevant on-premises devices. Configure the agent settings to align with the security policies of the hybrid environment. This ensures compliance with the hybrid environment’s security posture.
- Cloud Deployment: Configure the cloud-based components of Microsoft Defender for Endpoint, including the required policies, rules, and alerts. Establish the connection between the on-premises and cloud-based components to facilitate data exchange.
- Testing and Validation: Conduct thorough testing to validate the functionality and effectiveness of the deployed solution in the hybrid environment. This ensures that the security solution functions correctly across the hybrid cloud environment.
- Monitoring and Maintenance: Continuously monitor the deployed solution for performance and effectiveness. Regularly update the solution and adapt security policies as needed to maintain optimal security in the hybrid environment.
Access Control Configuration
Defining and managing access controls is critical for securing Microsoft Defender for Endpoint. Policies should be implemented to restrict access to sensitive data and prevent unauthorized actions. Roles and permissions should be clearly defined for administrators and users, ensuring only authorized personnel can manage the solution. This configuration ensures the security and integrity of the solution’s functionality.
Deployment Scenarios and Best Practices
The following table Artikels different deployment scenarios and corresponding best practices for Microsoft Defender for Endpoint:
| Deployment Scenario | Best Practices |
|---|---|
| On-premises | Prioritize agent-based deployment for comprehensive protection. Implement robust endpoint security policies to mitigate vulnerabilities. Ensure compliance with existing security frameworks. |
| Cloud | Leverage the cloud-native capabilities of Microsoft Defender for Endpoint. Utilize automation and orchestration tools to streamline deployment and management. Prioritize centralized security management. |
| Hybrid | Implement a phased approach to deployment, starting with a pilot program. Establish clear communication channels between on-premises and cloud teams. Ensure consistent security policies across both environments. Utilize security information and event management (SIEM) for unified threat detection and response. |
Advanced Features
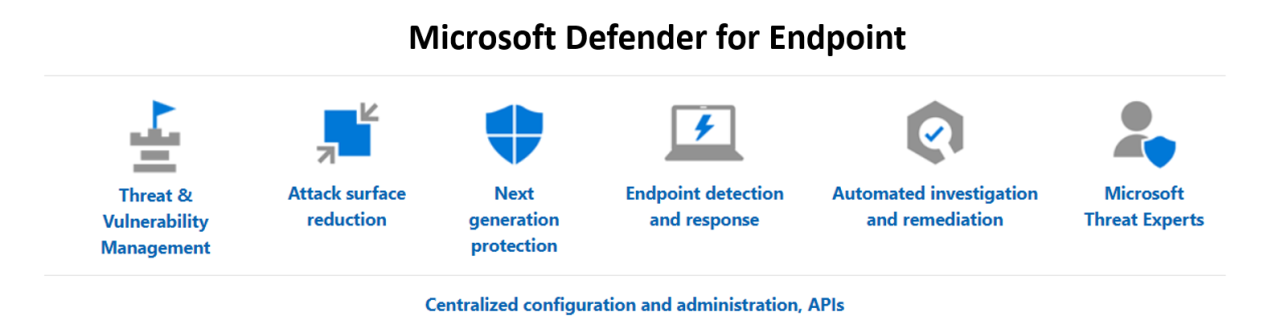
Microsoft Defender for Endpoint isn’t just about basic security; it’s a powerhouse of advanced features designed to proactively identify and neutralize sophisticated threats. From leveraging machine learning to bolstering vulnerability management, it’s a comprehensive solution that adapts to the ever-evolving threat landscape. This section dives deep into these advanced capabilities, providing a practical understanding of how they can protect your systems.
Threat Intelligence Sharing
Microsoft Defender for Endpoint leverages a vast network of threat intelligence, constantly updated and refined by Microsoft’s global threat detection network. This constant monitoring allows for real-time threat identification and response, enabling the solution to adapt to evolving attack strategies. This proactive approach is crucial in today’s dynamic cyber landscape. The shared intelligence helps identify patterns and trends in malicious activity, allowing for quicker response times and the mitigation of potential threats before they even materialize.
Vulnerability Management
Microsoft Defender for Endpoint’s vulnerability management features go beyond simple identification. It proactively assesses and prioritizes vulnerabilities, providing actionable insights for remediation. This empowers organizations to address potential weaknesses before attackers exploit them. The automated patching and configuration management capabilities further bolster security posture, minimizing the attack surface. This proactive approach is crucial for minimizing downtime and reputational damage.
Zero Trust Features
The solution’s zero trust capabilities are central to its advanced functionality. It enforces strict access controls, verifying every user and device before granting access to resources. This granular approach reduces the risk of unauthorized access and minimizes the impact of a breach. This enhanced security posture is critical in preventing lateral movement and containing damage if an attacker gains a foothold.
Ransomware Protection
Microsoft Defender for Endpoint actively defends against ransomware attacks through various mechanisms. It detects and blocks suspicious activities, such as encryption attempts, and isolates affected systems to contain the spread of ransomware. This proactive approach to threat detection and response minimizes the damage and recovery time associated with ransomware attacks. It works by actively monitoring file system activity, identifying anomalies, and isolating potentially compromised systems.
Advanced Persistent Threat (APT) Mitigation
Microsoft Defender for Endpoint helps mitigate advanced persistent threats (APTs) by detecting unusual and persistent activity patterns. It identifies and analyzes suspicious user behavior, unusual network traffic, and malicious code execution to pinpoint APT activities. The solution uses advanced analytics and machine learning to detect indicators of compromise (IOCs) that often go unnoticed by traditional security tools. This advanced approach is crucial in recognizing and neutralizing APTs, which are notoriously difficult to detect and respond to.
Security Feature Overview
| Feature | Description |
|---|---|
| Threat Intelligence | Leverages Microsoft’s global threat intelligence network for real-time threat identification and proactive response, adapting to evolving attack strategies. |
| Vulnerability Management | Proactively assesses and prioritizes vulnerabilities, providing actionable insights for remediation, automated patching, and configuration management. |
| Zero Trust Capabilities | Enforces strict access controls, verifying every user and device before granting access to resources, reducing the risk of unauthorized access and minimizing breach impact. |
| Ransomware Protection | Detects and blocks suspicious activities, such as encryption attempts, and isolates affected systems to contain the spread of ransomware, minimizing damage and recovery time. |
| APT Mitigation | Detects unusual and persistent activity patterns, identifying and analyzing suspicious user behavior, network traffic, and malicious code execution to pinpoint APT activities, using advanced analytics and machine learning to detect IOCs. |
Scenario-Based Demonstrations
Microsoft Defender for Endpoint isn’t just another security tool; it’s a proactive partner in your digital defense. Imagine a fortress constantly monitoring the perimeter, identifying threats before they breach, and swiftly responding to any infiltration. This section dives into real-world scenarios, showcasing how Defender for Endpoint works in action.
Defender for Endpoint isn’t passive; it’s a dynamic system that learns and adapts. Its intelligence isn’t static; it evolves with the ever-changing landscape of cyber threats. This adaptability allows it to effectively counter sophisticated attacks, safeguarding your systems and data.
Ransomware Prevention
Defender for Endpoint’s advanced threat protection capabilities actively scan for and block malicious activities, including ransomware. In a scenario where a user unknowingly clicks on a malicious link in an email, Defender for Endpoint’s cloud-based threat intelligence immediately flags the suspicious activity. Real-time monitoring prevents the execution of ransomware, isolating the infected files and alerting the administrator. This proactive response stops the ransomware from encrypting critical data and crippling operations.
Zero-Day Exploit Response
Zero-day exploits, previously unknown vulnerabilities, pose a significant threat. Defender for Endpoint’s machine learning algorithms and behavioral analysis capabilities continuously monitor for suspicious activity, even in unfamiliar code. If a zero-day exploit is detected, Defender for Endpoint can immediately block the malicious process and isolate the affected system. This rapid response mitigates the damage and prevents the exploit from spreading further.
Compliance Maintenance
Maintaining compliance with industry standards like HIPAA or PCI DSS is crucial. Defender for Endpoint integrates seamlessly with existing compliance tools and processes. Detailed logs and reports generated by Defender for Endpoint allow administrators to demonstrate compliance with regulations. By providing evidence of security measures, organizations can avoid penalties and maintain a strong security posture.
Suspicious Email Reporting
Users often encounter suspicious emails. When a user reports a suspicious email, Defender for Endpoint’s security intelligence is immediately alerted. The email is analyzed for malicious content, attachments, and links. If a threat is identified, Defender for Endpoint quarantines the email and notifies the user. This proactive response protects the entire network from potential threats.
Vulnerability Identification and Remediation
Defender for Endpoint proactively scans systems for known and unknown vulnerabilities. If a vulnerability is identified, Defender for Endpoint provides detailed information about the vulnerability, including its severity and potential impact. Defender for Endpoint can also suggest remediation steps, such as patching or configuring security settings, to mitigate the risk. This automated approach minimizes the window of vulnerability and reduces the likelihood of a successful attack.
Final Summary
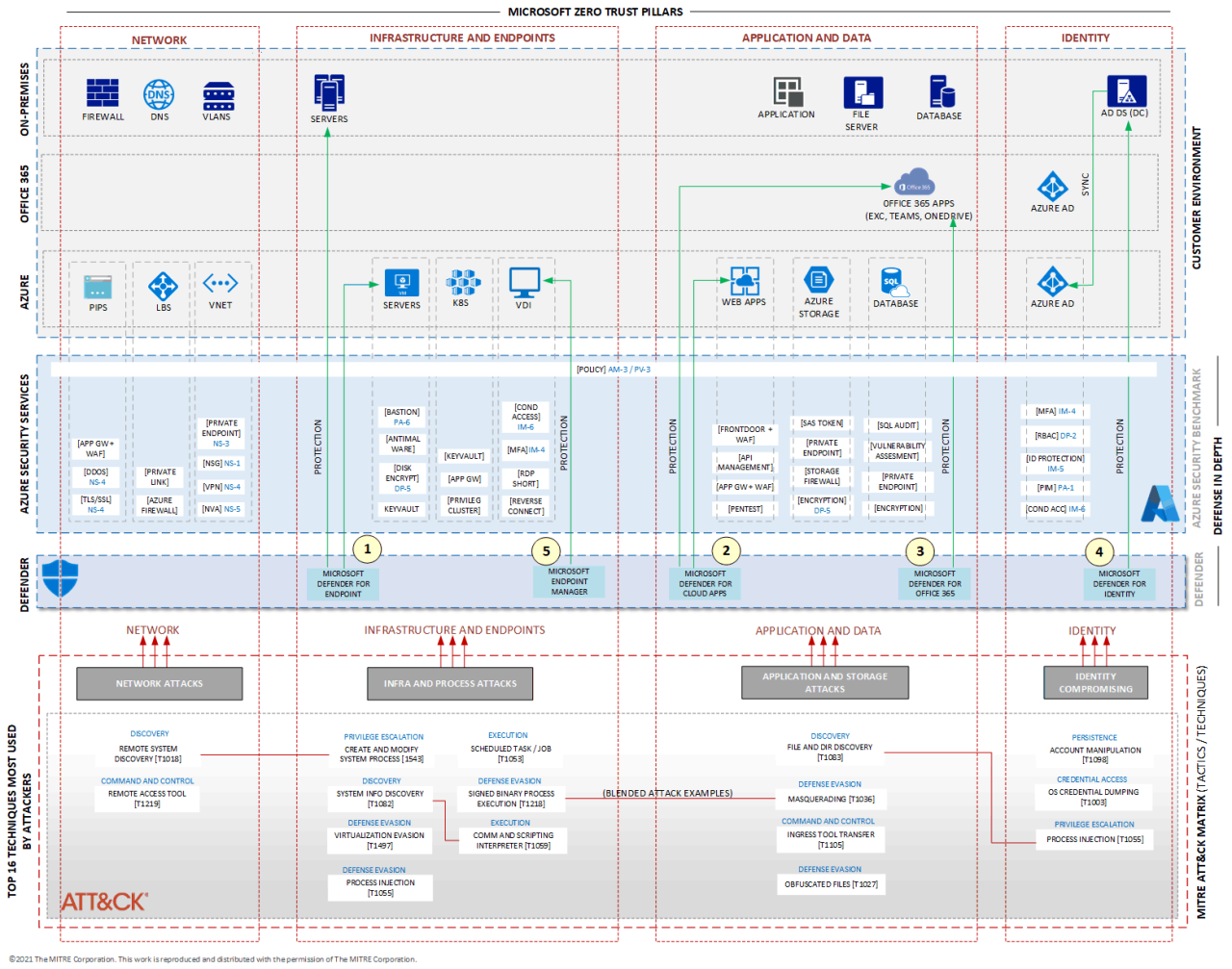
Jadi, Microsoft Defender for Endpoint ini adalah solusi keamanan yang komprehensif, andal, dan mudah dipake. Dari perlindungan real-time sampai manajemen dan monitoring, semua ada di sini. Dengan berbagai fitur dan deployment option yang tersedia, Defender ini jadi pilihan tepat untuk melindungi semua perangkat dan data ente. Semoga informasi ini bermanfaat buat ente semua!