Welcome to the thrilling world of advanced port scanners! Imagine a digital detective, equipped with cutting-edge tools, meticulously probing the hidden nooks and crannies of a network. This isn’t your grandpa’s simple port scanner; we’re talking about sophisticated instruments capable of uncovering vulnerabilities, mapping networks, and even predicting potential cyberattacks. Get ready to explore the fascinating realm where technology meets security!
This exploration delves into the core functionalities of advanced port scanners, examining their capabilities beyond basic port discovery. We’ll analyze various protocols and services they can scrutinize, revealing the intricate dance between network traffic and security vulnerabilities. Discover the tools used for efficient network mapping, from simple TCP/IP scans to advanced techniques for identifying hidden services and vulnerabilities. Prepare to be amazed by the power of these digital detectives!
Introduction to Advanced Port Scanners
Advanced port scanners represent a sophisticated evolution of network reconnaissance tools, moving beyond basic port discovery to encompass deeper analysis and vulnerability assessment. These tools are crucial for cybersecurity professionals, enabling proactive identification and mitigation of potential threats. Their capabilities extend beyond simple port enumeration, providing critical insights into the security posture of target systems.
The core difference between basic and advanced port scanners lies in their analytical depth and functionality. Basic scanners primarily identify open ports, while advanced scanners go further, probing for vulnerabilities and understanding the underlying network architecture. This difference is critical in today’s complex threat landscape, where attackers are constantly developing more sophisticated tactics.
Key Differences Between Basic and Advanced Port Scanners
Basic port scanners focus on identifying open ports on a target system. They typically use simple scanning techniques, such as TCP connect scans or SYN scans, and provide minimal information about the services running on those ports. Advanced port scanners, conversely, incorporate more sophisticated techniques, analyze the responses from target systems, and often integrate with vulnerability databases. This detailed approach allows for a more comprehensive understanding of potential security weaknesses.
Types of Advanced Port Scanners
Advanced port scanners encompass a range of specialized tools. Vulnerability scanners, for example, are designed to identify known security vulnerabilities on systems and applications. These tools leverage databases of known vulnerabilities to assess the potential risk associated with exposed services. Network mappers, another category, focus on charting the structure and layout of a network, allowing administrators to visualize the relationships between devices and services.
Features Distinguishing Advanced Port Scanners
Advanced port scanners possess several features that set them apart from their basic counterparts. These include deeper probing of open ports, the ability to detect specific vulnerabilities based on known signatures, and integration with security databases to provide context for identified vulnerabilities. They often include more advanced scanning techniques like stealth scans and evasion techniques to avoid detection. Moreover, many advanced scanners provide detailed reports, making it easier to understand and prioritize security issues.
Comparison of Basic and Advanced Port Scanners
| Feature | Basic Port Scanner | Advanced Port Scanner |
|---|---|---|
| Speed | Generally faster for basic port scans. | Slower, but more thorough. Accuracy and thoroughness are prioritized over speed. |
| Accuracy | Limited accuracy; may miss vulnerabilities or provide inaccurate information. | High accuracy due to more sophisticated techniques and data analysis. |
| Complexity | Relatively simple to use. | More complex, often requiring specialized knowledge for optimal use. |
| Functionality | Primarily identifies open ports. | Identifies open ports, vulnerabilities, and provides detailed network mapping. |
| Reporting | Basic, often just a list of open ports. | Comprehensive, including detailed reports on identified vulnerabilities, risk assessments, and network diagrams. |
Functionality and Capabilities
Advanced port scanners transcend the basic function of simply identifying open ports. They delve deeper into network infrastructure, probing for vulnerabilities and weaknesses that could be exploited by malicious actors. This sophisticated approach allows security teams to proactively address potential threats, significantly bolstering network defenses.
Beyond basic port discovery, these scanners offer a suite of advanced functionalities, extending far beyond identifying open ports. They are designed to assess the security posture of a network, identify potential weaknesses, and provide insights into the overall health of the infrastructure. This proactive approach to security assessment allows organizations to identify and address potential vulnerabilities before they are exploited.
Vulnerability Identification
Advanced port scanners utilize a combination of techniques to identify vulnerabilities. They probe services for known vulnerabilities, exploiting weaknesses in protocols or configurations. This sophisticated probing allows security professionals to identify misconfigurations, outdated software, and other weaknesses in a systematic and thorough manner. The information gathered during these scans is crucial for understanding the overall security posture of a network and for prioritising remediation efforts.
Protocol and Service Analysis
Advanced port scanners can analyze a broad spectrum of protocols and services. These tools often include modules for examining specific protocols like FTP, SSH, HTTP, and various database services. They are designed to identify vulnerabilities in configurations or implementations of these protocols. This capability allows for a comprehensive security assessment that goes beyond simple port scanning.
Security Audits
Advanced port scanners are invaluable tools for security audits. They can provide a detailed inventory of services running on a network, identify misconfigurations, and pinpoint potential security gaps. This comprehensive approach allows security teams to create a detailed report that can be used to prioritize remediation efforts and ensure compliance with security standards.
Network Reconnaissance
Advanced port scanners can be employed for network reconnaissance. By identifying open ports and services, these scanners can provide valuable information about the network architecture, infrastructure, and potential vulnerabilities. This information can be used to develop a more comprehensive security strategy, identifying weak points in the network’s defense.
Detailed Protocol and Service Analysis
| Protocol | Service | Example |
|---|---|---|
| TCP | HTTP | Web server |
| TCP | SSH | Secure Shell |
| TCP | FTP | File Transfer Protocol |
| UDP | DNS | Domain Name System |
| TCP | SMTP | Simple Mail Transfer Protocol |
| TCP | Telnet | Text-based network terminal protocol |
| TCP | MySQL | Relational Database Management System |
| TCP | PostgreSQL | Object-Relational Database System |
Advanced port scanners can analyze a vast array of protocols and services, providing detailed insights into the network’s configuration and potential vulnerabilities. The table above provides a sample of the protocols and services that can be scanned. The exact list can vary depending on the specific scanner.
Techniques and Methods
Advanced port scanners are no longer limited to basic TCP/IP port scans. Modern tools employ sophisticated techniques to map networks efficiently, identify hidden services, and uncover vulnerabilities. These methods, ranging from stealthy probing to intricate protocol analysis, provide crucial intelligence for security assessments and threat modeling. The effectiveness of these techniques often depends on the specific network architecture and the vulnerabilities present.
Modern network security relies heavily on the sophistication of these scanning tools. The ability to identify vulnerabilities before attackers can exploit them is a key element in proactive security strategies. Understanding the various scanning methodologies and their limitations is essential for effective defense.
Advanced Scanning Techniques
Advanced scanning techniques move beyond simple port scans to analyze network structures and identify subtle anomalies. These techniques can uncover hidden services, misconfigurations, and vulnerabilities that might otherwise remain undetected. Understanding the strengths and weaknesses of different scanning methodologies is crucial for tailoring the approach to the specific network environment.
Stealth Scanning Techniques
Stealth scanning techniques aim to evade detection by firewalls and intrusion detection systems. They achieve this by using various methods, including spoofing source IP addresses, fragmenting packets, and employing different scanning patterns. These methods make it harder for the target system to identify and block the scan. Examples include SYN stealth scans, which only send the SYN packet and wait for the response, and FIN/ACK scans, which send FIN and ACK packets to probe the target.
Vulnerability Scanning Techniques
Identifying vulnerabilities requires more than just port scanning. Vulnerability scanning techniques actively probe for known weaknesses in software and configurations. These methods involve using specialized scripts and libraries to simulate attacks, identify vulnerabilities, and provide recommendations for remediation. A common example involves probing for known vulnerabilities in web servers. Automated tools often use databases of known vulnerabilities to identify potential exploits and provide information about the risks involved.
Protocol-Specific Scanning
Beyond TCP/IP, advanced scanners often probe specific protocols. This allows for a more in-depth analysis of the network infrastructure and the services running on it. Scanning techniques may include DNS enumeration to map domain names to IP addresses, SNMP scanning to gather information about network devices, or SMB scanning to probe for vulnerabilities in file sharing protocols.
Hidden Service Detection
Hidden services, often used for illicit activities, are designed to avoid detection by conventional scanning methods. Advanced scanners use specific techniques to uncover these services. These techniques involve analyzing network traffic patterns and identifying unusual activity. Examples include using specific port ranges for dark web or Tor services, or looking for encrypted communications over unusual protocols.
Comparison of Scanning Methodologies
| Method | Target | Speed | Limitations |
|---|---|---|---|
| SYN Stealth Scan | Open TCP ports | Faster than basic scans | Can be blocked by SYN cookies |
| FIN/ACK Scan | Open or closed TCP ports | Moderate speed | Can trigger IDS/IPS alerts |
| Vulnerability Scan | Software and configuration weaknesses | Variable speed | Reliance on vulnerability databases, false positives |
| Protocol-Specific Scan (e.g., SNMP) | Specific network devices and protocols | Moderate to slow | Requires knowledge of the specific protocol |
Practical Applications and Use Cases
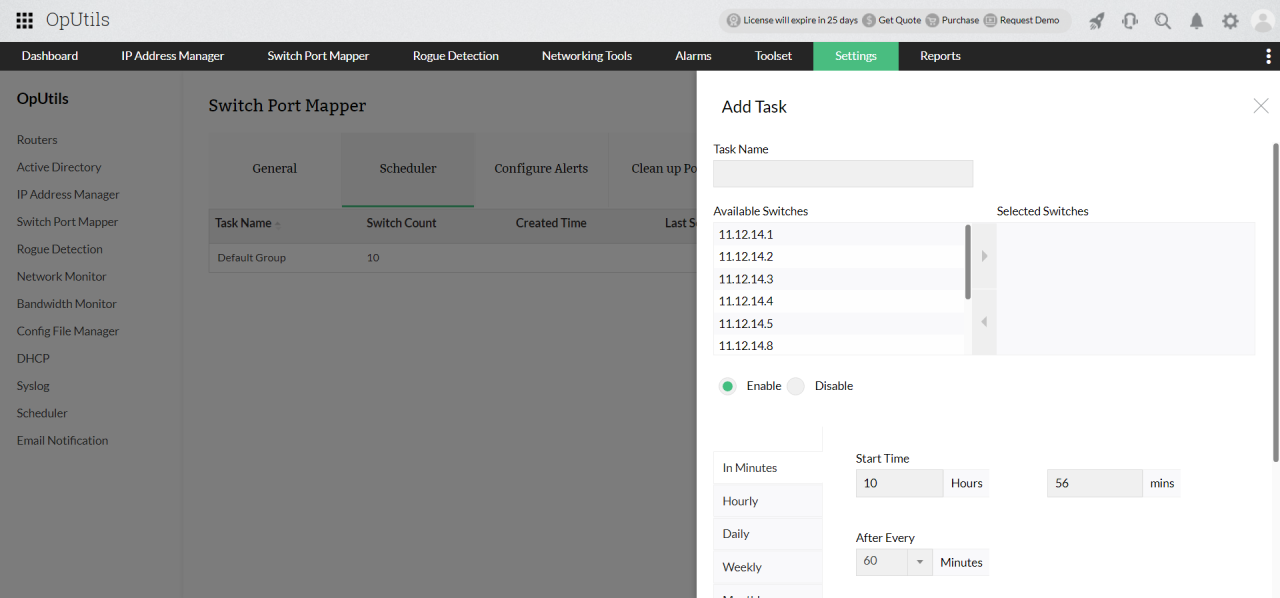
Advanced port scanners are indispensable tools in the modern cybersecurity landscape, moving beyond basic port scanning to provide detailed insights into network vulnerabilities. Their sophisticated functionalities empower security professionals to proactively identify and mitigate risks before they escalate into significant breaches. These scanners are critical for penetration testing, network security assessments, and the overall fortification of digital infrastructure.
Advanced port scanners go beyond simply identifying open ports. They delve deeper, probing the underlying services running on those ports, evaluating the versions of software in use, and analyzing the responses to determine potential security weaknesses. This deeper analysis allows for a more comprehensive understanding of the vulnerabilities present in a network, enabling proactive security measures and ultimately preventing potential cyberattacks.
Penetration Testing
Penetration testing simulates real-world attacks to evaluate the security posture of a system or network. Advanced port scanners are integral to this process, used to identify potential entry points. By meticulously probing for vulnerabilities, these scanners help penetration testers understand the attack surface, assess the risk level, and recommend appropriate remediation strategies. This proactive approach is crucial for organizations seeking to strengthen their defenses against sophisticated threats.
Network Security Assessments
Regular network security assessments are critical for maintaining a strong security posture. Advanced port scanners play a pivotal role in these assessments by identifying open ports and potential misconfigurations. They offer a systematic method for discovering vulnerabilities, allowing security teams to prioritize remediation efforts and reduce the attack surface. This data-driven approach ensures that security measures are aligned with the actual risks faced by the network.
Identifying Security Gaps and Weaknesses
Advanced port scanners meticulously identify security gaps by uncovering vulnerabilities in software versions, misconfigurations, and weak security protocols. By analyzing the responses from scanned systems, these tools pinpoint inconsistencies that attackers could exploit. For instance, if a scanner detects an outdated web server version with known vulnerabilities, it flags this as a critical security gap that needs immediate attention. The detailed information provided facilitates targeted remediation efforts.
Proactive Security Measures
Proactive security measures are paramount in today’s threat landscape. Advanced port scanners are essential for implementing these measures. By proactively identifying vulnerabilities, organizations can implement security patches, configure firewalls more effectively, and bolster overall network defenses. This forward-thinking approach helps organizations stay ahead of evolving threats, minimizing the risk of costly data breaches and reputational damage.
Use Cases for Advanced Port Scanners
| Use Case | Target | Expected Outcome |
|---|---|---|
| Identifying Vulnerable Services | Corporate Network | Identification of servers running outdated or vulnerable versions of services. |
| Penetration Testing | Web Application | Discovery of potential vulnerabilities in web applications, like SQL injection or cross-site scripting. |
| Network Security Audit | Firewall | Detailed analysis of firewall rules and configuration to identify potential bypasses or weaknesses. |
| Proactive Vulnerability Management | IoT Devices | Identification of vulnerable IoT devices and potential risks to the network. |
| Security Assessment of Third-Party Vendors | External Network | Assessment of the security posture of external network infrastructure, revealing potential vulnerabilities and risks. |
Security Considerations and Ethical Implications
Advanced port scanners, while powerful tools for network analysis and security assessments, carry significant ethical and legal responsibilities. Misuse of these tools can lead to serious consequences, ranging from legal repercussions to reputational damage. Understanding the ethical implications and potential risks is paramount for responsible use.
The capabilities of advanced port scanners allow for in-depth network exploration, but this power necessitates a careful consideration of the potential for harm if not employed ethically. Unauthorized scans can cause significant disruption and breach the security posture of targeted systems, violating the trust and privacy of individuals and organizations.
Ethical Considerations of Advanced Port Scanner Use
Employing advanced port scanners responsibly requires adherence to strict ethical guidelines. Unauthorized scans constitute a violation of privacy and potentially breach legal frameworks. Prior authorization is crucial before initiating any network exploration.
Potential Risks and Dangers of Misuse
Misusing advanced port scanners can result in severe repercussions. Unauthorized scans may lead to legal penalties, including hefty fines and criminal charges. Furthermore, these actions can severely damage the reputation of individuals or organizations involved, impacting future prospects and trust. Examples include a breach of a hospital’s network, potentially jeopardizing patient records, or disrupting critical infrastructure, like power grids.
Legal Implications of Unauthorized Scans
Unauthorized use of advanced port scanners is often illegal, depending on jurisdiction. Laws surrounding cybercrime and network security vary globally, and engaging in such activities can result in criminal prosecution. Depending on the severity of the unauthorized scans and potential damages, the consequences can range from hefty fines to imprisonment.
Importance of Obtaining Proper Authorization
Prior authorization is crucial for conducting any network scans. This authorization should explicitly define the scope of the scan, the targeted systems, and the permissible actions. Failure to obtain proper authorization can lead to severe legal and ethical ramifications. Clear contractual agreements and explicit consent are critical for lawful and ethical operations.
Table of Potential Risks and Ethical Concerns
| Risk | Impact | Mitigation Strategies |
|---|---|---|
| Unauthorized access to sensitive data | Data breaches, reputational damage, legal repercussions | Obtain explicit authorization from system owners, adhere to strict privacy regulations, secure scanned data, maintain comprehensive audit logs. |
| Disruption of network services | Downtime, loss of productivity, financial losses | Employ controlled scanning methods, avoid targeting critical infrastructure without authorization, adhere to service level agreements. |
| Violation of privacy | Reputational damage, legal issues, erosion of public trust | Obtain explicit consent from data owners, respect privacy policies, comply with relevant regulations. |
| Financial penalties | Significant fines, legal fees, and potential imprisonment | Obtain explicit authorization from system owners, maintain detailed documentation of scanning activities, comply with all relevant laws and regulations. |
Advanced Port Scanner Examples and Tools
Advanced port scanners are critical tools for network security professionals, enabling them to identify vulnerabilities and assess the security posture of systems. Beyond basic port scanning, these sophisticated tools often incorporate advanced techniques like vulnerability detection and service fingerprinting, providing a more comprehensive security assessment. This exploration delves into several prominent examples, highlighting their features, strengths, and limitations.
Modern network environments demand tools that can go beyond simple port discovery. Advanced port scanners not only identify open ports but also attempt to understand the services running behind them, potentially revealing weaknesses that simple scanners might miss. The ability to differentiate between legitimate services and potential vulnerabilities is crucial for proactive security management.
Prominent Advanced Port Scanners
Several tools excel in the advanced port scanning arena, each with its own strengths and weaknesses. Choosing the right tool depends on the specific needs and objectives of the security assessment.
- Nmap: A widely recognized open-source port scanner, Nmap offers a robust suite of features, including comprehensive port scanning, version detection, operating system fingerprinting, and service identification. Its versatility, coupled with its extensive documentation and large community support, makes it a popular choice for both beginners and experts. Nmap’s versatility is its strength, as it can be adapted to various scenarios, from basic port scans to complex network analyses.
- OpenVAS: This open-source vulnerability scanner, based on the Nessus engine, allows for thorough network assessments. OpenVAS enables in-depth analysis of discovered services, identifying potential vulnerabilities and providing detailed reports. Its ability to integrate with other security tools and its modular architecture contributes to its widespread use in professional security environments.
- Nessus Professional: This commercial vulnerability scanner is renowned for its comprehensive vulnerability database and sophisticated analysis capabilities. Nessus Professional provides detailed information about discovered vulnerabilities, enabling organizations to prioritize remediation efforts effectively. Its strong reporting features, coupled with its advanced scanning techniques, makes it a valuable asset for enterprise-level security assessments. Its comprehensive database of vulnerabilities is a key strength.
- QualysGuard: This commercial platform is a comprehensive security management solution that includes an advanced port scanner. It provides a centralized platform for managing security risks across the entire organization, enabling continuous monitoring and reporting. QualysGuard’s ability to integrate with other security tools and provide comprehensive reporting makes it a preferred choice for large enterprises.
Key Features and Functionalities
Advanced port scanners go beyond simple port discovery to offer comprehensive insights into network security. These features aid in identifying potential weaknesses and vulnerabilities.
| Tool Name | Key Features | Limitations |
|---|---|---|
| Nmap | Comprehensive port scanning, version detection, operating system fingerprinting, script engine, and detailed output | Can be resource-intensive for large networks, requires some technical expertise |
| OpenVAS | Thorough vulnerability scanning, extensive vulnerability database, integration with other security tools | OpenVAS can be less user-friendly than some commercial options, and requires periodic updates to maintain its database |
| Nessus Professional | Extensive vulnerability database, sophisticated analysis capabilities, detailed reporting, and prioritization of vulnerabilities | Commercial license required, potential cost constraints for smaller organizations |
| QualysGuard | Centralized security management platform, continuous monitoring, integration with other tools, and comprehensive reporting | Primarily a comprehensive security management platform, may not be ideal for a very focused port scan |
Tools and Websites
The following table provides links to the websites of some prominent advanced port scanning tools.
- Nmap: https://nmap.org
- OpenVAS: https://www.openvas.org
- Nessus Professional: https://www.tenable.com/products/nessus
- QualysGuard: https://www.qualys.com/products/qualysguard.html
Illustrative Scenarios and Demonstrations
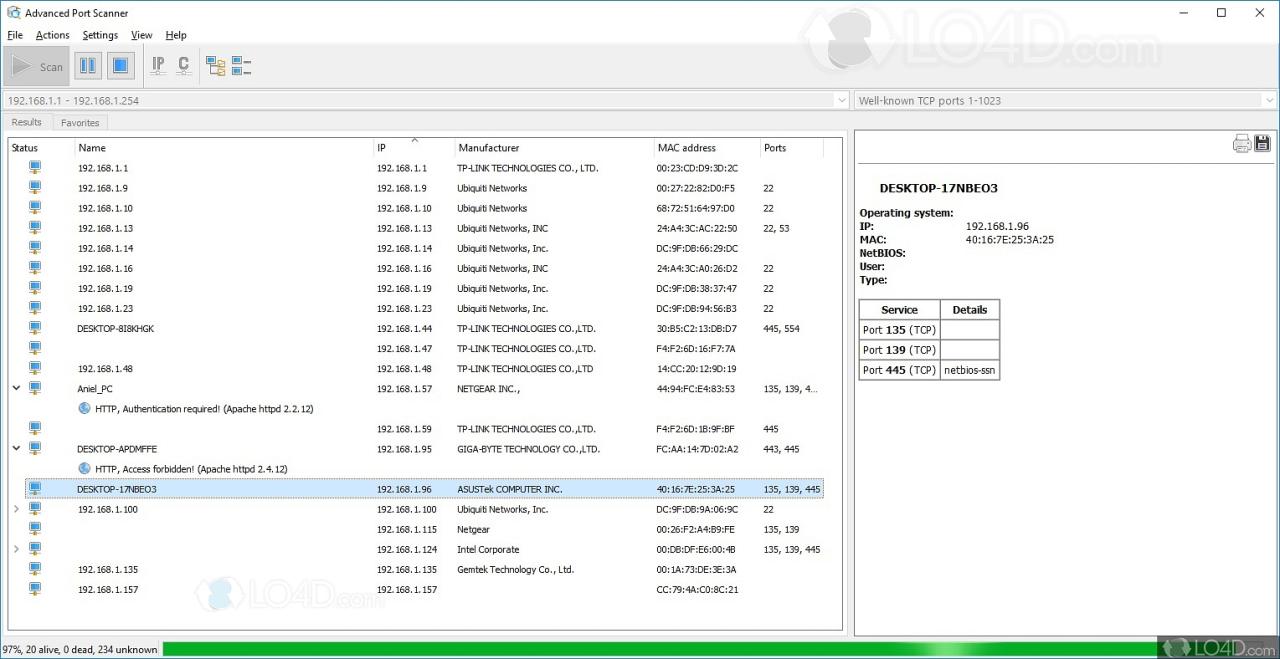
Advanced port scanners are invaluable tools for network security professionals, allowing for proactive identification and remediation of vulnerabilities. This section provides illustrative scenarios demonstrating how these scanners operate, highlighting their ability to detect weaknesses and guide mitigation efforts. These demonstrations are crucial for understanding the practical application of advanced port scanning techniques.
Vulnerability Detection Scenario
A hypothetical enterprise network, “Acme Corp,” utilizes a custom application running on port 8080. An advanced port scanner, employing sophisticated fingerprinting techniques, identifies a previously unknown vulnerability in the application’s handling of authentication requests. The scanner’s deep analysis reveals a flaw in the server’s response to specific input patterns, allowing unauthorized access to sensitive data.
Vulnerability Analysis
The scanner meticulously scrutinizes the server’s responses to various input sequences, identifying patterns that trigger the vulnerability. This process involves packet analysis, protocol decoding, and comparison against known attack vectors. The scanner detects the specific input pattern causing the server to reveal information that could be exploited for malicious purposes. The detailed analysis provides crucial insights into the vulnerability’s root cause and potential impact.
Mitigation Steps
Upon identifying the vulnerability, Acme Corp immediately implements corrective actions. This involves patching the vulnerable application, strengthening authentication protocols, and implementing robust input validation measures. These steps ensure the vulnerability is sealed, preventing exploitation by malicious actors.
Network Scanning Demonstration
Consider a network with three devices: a web server (192.168.1.100), a database server (192.168.1.101), and a file server (192.168.1.102). An advanced port scanner, running on a secure workstation, scans the network, probing each device for open ports and services.
Scanner Functionality
The scanner initiates the scan by sending connection requests to each device on the network. The scanner meticulously probes each open port, using techniques like TCP SYN scans, to determine the nature of the service running on that port. In this scenario, the scanner detects that port 80 (HTTP) and port 22 (SSH) are open on the web server, and port 3306 (MySQL) is open on the database server.
- The scanner sends a SYN packet to the web server’s port 80. The server responds with a SYN-ACK, indicating the port is open.
- The scanner repeats this process for other ports on the web server and the other two devices.
- The scanner then employs fingerprinting techniques to determine the specific services running on the open ports, for example, identifying Apache as the web server.
- The scanner generates a report detailing the open ports, services, and operating systems of each device on the network.
Sample Scanner Output
Network Scan Report - Acme Corp Date: 2024-10-27 Target: 192.168.1.0/24 Device: 192.168.1.100 (Web Server) Open Ports: 80 (HTTP), 22 (SSH) Service: Apache 2.4.50, Linux Operating System: Debian 11 Device: 192.168.1.101 (Database Server) Open Ports: 3306 (MySQL) Service: MySQL 8.0.33 Operating System: CentOS 8 Device: 192.168.1.102 (File Server) Open Ports: 445 (SMB) Service: Samba 4.13.12 Operating System: Windows Server 2019
Advanced Port Scanner Architecture and Components
Advanced port scanners, crucial tools in network security assessments, are increasingly sophisticated, demanding a deeper understanding of their internal workings. This intricate architecture enables these scanners to efficiently identify open ports, determine services running on those ports, and assess vulnerabilities. Understanding the components and their interplay is essential for both deploying and evaluating these powerful tools.
Modern advanced port scanners employ a modular design, fostering flexibility and adaptability. This modularity allows for the incorporation of new scanning techniques and the expansion of capabilities without significantly altering the core architecture. Key components and their interaction form the foundation of this robust design.
High-Level Architecture Overview
The architecture of a typical advanced port scanner resembles a layered system, each layer contributing to the overall functionality. This layered structure enhances efficiency by separating tasks and enabling parallel operations. The core components typically include a control module, a scanning engine, a data processing unit, and a reporting module.
Components and Interactions
- Control Module: This module acts as the central nervous system, coordinating all activities. It receives user-defined scanning parameters, such as target hosts, ports to scan, and scan types. It then directs the scanning engine and manages the data flow throughout the system. This module prioritizes tasks and allocates resources, ensuring optimal scanning efficiency.
- Scanning Engine: This engine houses the core scanning logic. It implements various scanning techniques, including TCP connect scans, SYN scans, and UDP scans. The engine directly interacts with the target network, sending probes and collecting responses. Sophisticated scanners often use techniques like parallel scanning to expedite the process and handle large-scale scans.
- Data Processing Unit: This component processes the data received from the scanning engine. It analyzes the responses to identify open ports, determine the services running on those ports, and detect any potential vulnerabilities. The data processing unit often incorporates pattern recognition algorithms and signature databases to accelerate the identification process.
- Reporting Module: This module compiles the collected data and presents it in a structured format. The report often includes a detailed list of open ports, the services associated with them, and any detected vulnerabilities. Advanced scanners might provide interactive dashboards and visualization tools for better comprehension of the scan results.
Data Flow
The data flow within the advanced port scanner architecture is typically unidirectional, from the control module to the scanning engine, then to the data processing unit, and finally to the reporting module. The control module provides the instructions, the scanning engine executes them, the data processing unit analyzes the results, and the reporting module presents the output to the user. Real-time feedback loops can exist within the data processing unit to inform the control module of potential issues or irregularities, leading to more targeted scans.
Illustrative Architecture Diagram
Imagine a layered cake, with each layer representing a crucial component. The top layer is the control module, managing the overall process. Beneath it lies the scanning engine, responsible for the direct interaction with target hosts. The data processing unit sits in the middle, analyzing the responses. Finally, the reporting module, the last layer, presents the findings to the user in a comprehensive report. This layered architecture ensures efficiency and accuracy, allowing the scanner to efficiently navigate through the network to discover potential vulnerabilities.
Summary

In conclusion, advanced port scanners are invaluable tools for network security assessments. They allow for proactive identification of security gaps, empowering users to bolster their defenses against potential threats. This deep dive into their functionalities, techniques, and applications provides a comprehensive understanding of their capabilities. From vulnerability detection to penetration testing, these tools empower security professionals to navigate the complex landscape of network security. Embrace the power of these advanced scanners and keep your networks safe and sound!