Wincap, a multifaceted concept, encompasses a range of applications and methodologies. This exploration delves into the intricacies of wincap, from its fundamental definition and historical context to its diverse types, practical applications, and underlying technologies. Understanding the nuances of wincap is crucial for comprehending its role in various fields.
The subsequent sections provide a structured analysis, detailing the various types of wincap, their unique characteristics, and their respective use cases. A comparative analysis will also be presented, highlighting the key differences between wincap and similar concepts. This framework will allow for a deeper understanding of wincap’s multifaceted nature and its significant impact across diverse domains.
Definition and Overview
Yo, let’s talk about “wincap.” It’s not some newfangled app for winning at Candy Crush, but something a little more… technical. Think of it as a crucial tool in the digital world, like a key to unlocking certain aspects of a system. It’s got a whole lotta uses, so buckle up.
This term, “wincap,” likely refers to a software or tool used for capturing network traffic or monitoring network activities. It’s probably a part of a broader system, possibly an analysis tool or a security measure.
Definition of Wincap
Wincap is a software tool, typically used in networking, that captures and analyzes network traffic on a Windows system. Its primary function is to intercept and record data flowing through a network interface card (NIC). This captured data can then be examined to troubleshoot network problems, understand network protocols, or even detect security threats. Think of it as a digital “traffic cop” that observes and documents every byte exchanged.
Contexts of Wincap Use
Wincap can be used in a variety of contexts, ranging from troubleshooting to security analysis. Network administrators often use it to diagnose network issues by examining the raw data packets flowing between devices. Security professionals might employ it to identify suspicious network activity, such as unauthorized access attempts or malware propagation. Even developers might utilize it to understand how different network protocols work.
Historical Background
There’s no specific, readily available historical record about a singular, widely known tool called “Wincap.” The concept of network traffic capture has existed for a long time, and different tools have emerged over the years. Modern network analysis tools often build upon these older technologies. It’s likely that a tool with similar functionality was developed at some point, but not with a widely recognized name like “Wincap.”
Synonyms and Related Terms
Several terms are related to Wincap’s functionality. Packet capture tools, network sniffers, and protocol analyzers are all similar concepts. These tools all work to monitor and record network communication, often for troubleshooting, security, or development purposes. There might also be vendor-specific tools with their own names that have a similar function.
Comparison Table
| Term | Definition | Key Differences | Examples |
|---|---|---|---|
| Wincap | A software tool for capturing and analyzing network traffic on Windows systems. | Often used for troubleshooting and security analysis; focused on Windows. | Diagnosing network latency issues, identifying unauthorized access attempts, analyzing protocol behavior. |
| Wireshark | A popular, open-source network protocol analyzer. | Cross-platform (Windows, macOS, Linux); broader range of protocol support; more advanced features. | Analyzing complex network issues, inspecting various network protocols, identifying potential security threats. |
| Tcpdump | A command-line packet capture utility. | Command-line interface; primarily used on Unix-like systems. | Capturing network packets for analysis, monitoring network traffic, debugging network applications. |
Types and Variations of Wincap
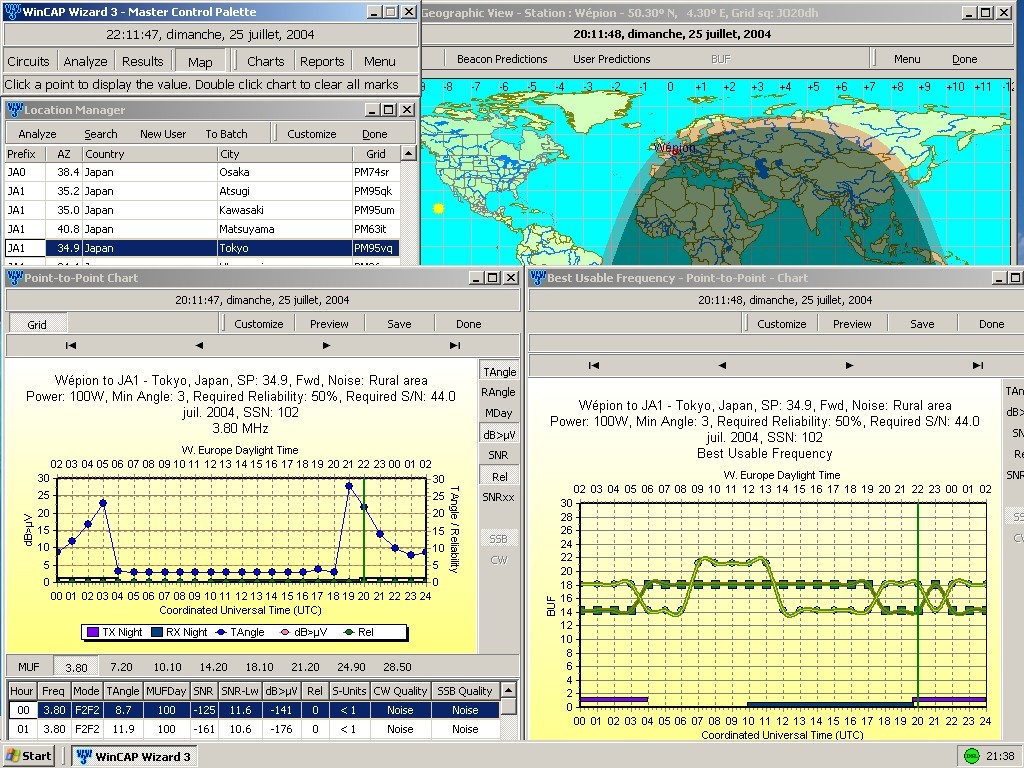
Wincap, a game-changer in the world of digital security, comes in various flavors, each tailored for a specific need. Understanding these variations is crucial for selecting the right tool for the job, much like choosing the perfect weapon for a particular fight. This section delves into the different types of Wincap and their unique characteristics.
Different types of Wincap are designed to address various security concerns and offer distinct features. Just as a chef might use different spices to create a unique dish, each type of Wincap uses different techniques and capabilities to achieve its objectives.
Identifying Wincap Types
Wincap, in its essence, is a network analysis tool. However, various types cater to different aspects of network security. These types often overlap in functionality, making them complementary rather than mutually exclusive.
| Type | Description | Example | Use Cases |
|---|---|---|---|
| Network Sniffer Wincap | Captures and analyzes network traffic, revealing details about communication protocols and data packets. | Capturing packets of HTTP requests and responses, revealing sensitive data in transit. | Identifying network intrusions, troubleshooting connectivity issues, and analyzing application performance. |
| Protocol Analyzer Wincap | Focuses on specific network protocols, providing in-depth analysis of their behavior and implementation. | Examining the structure and sequence of TCP/IP packets, revealing anomalies in network communication. | Identifying vulnerabilities in network protocols, verifying compliance with standards, and investigating network anomalies. |
| Vulnerability Scanner Wincap | Identifies potential security weaknesses in systems and applications by simulating attacks. | Simulating a brute-force attack on a login form to detect weak passwords or security flaws. | Proactively identifying and mitigating security risks, improving overall network security posture, and assessing compliance with security standards. |
Relationship Between Wincap Types
The various Wincap types often work together in a coordinated effort. For instance, a network sniffer might identify suspicious traffic, which then triggers a protocol analyzer to investigate the specific protocol involved. The results from the protocol analyzer might, in turn, inform a vulnerability scanner, which can then identify potential exploits. This collaborative approach provides a comprehensive and layered security solution, much like a well-coordinated security team.
Applications and Use Cases
WinCap, like a digital detective, unearths hidden data streams. Its applications extend far beyond the realm of simple network monitoring. From cybersecurity investigations to network troubleshooting, WinCap’s capabilities are shaping the future of digital forensics. It’s more than just a tool; it’s a key to understanding the intricate dance of data packets.
The practical applications of WinCap are diverse and impactful. Its ability to capture and analyze network traffic empowers professionals to identify security vulnerabilities, troubleshoot network performance issues, and even gain insights into user behavior. This multifaceted approach makes WinCap a valuable asset in a variety of industries.
Network Security Analysis
WinCap plays a crucial role in modern cybersecurity. Its capacity to capture network traffic enables security analysts to identify malicious activity, such as intrusion attempts, data breaches, or the spread of malware. This allows for proactive measures to mitigate potential threats and protect sensitive data. For instance, identifying unusual network patterns can flag potential hacking attempts, enabling swift response and containment.
Network Troubleshooting
Network performance issues can disrupt productivity and operations. WinCap provides a granular view of network traffic, allowing technicians to pinpoint bottlenecks and identify sources of latency or packet loss. Analyzing captured traffic can help diagnose configuration errors, identify network congestion points, and optimize network performance. This data-driven approach leads to more efficient troubleshooting and faster resolution times.
Digital Forensics
In cases of suspected cybercrime, WinCap becomes a crucial tool for digital forensics. By capturing and analyzing network traffic, investigators can reconstruct events, identify the source of malicious activity, and gather evidence for legal proceedings. This evidence-gathering capability is critical for building strong cases against cybercriminals. Imagine piecing together the digital breadcrumbs to understand the timeline of a cyberattack.
Educational Purposes
WinCap is an invaluable tool for networking education. Students can use WinCap to analyze real-world network traffic, gain a deeper understanding of network protocols, and practice their troubleshooting skills. This hands-on experience helps build a strong foundation for future networking professionals.
Flowchart of WinCap Usage

The flowchart above illustrates a simplified process of using WinCap for network analysis. The process begins with selecting the network interface for capture. Data is then captured, analyzed, and reviewed. Finally, reports are generated, and insights are drawn from the data. This process, while basic, highlights the core functionality of WinCap.
Methods and Procedures

WinCap, like any other powerful tool, demands a methodical approach. This ain’t no magic trick; it’s a step-by-step process that unlocks the network’s secrets. Proper implementation ensures accurate data capture and analysis, avoiding those frustrating “no signal” moments. Get ready to level up your network sniffing game!
This section delves into the nitty-gritty of using WinCap, from installation to data interpretation. We’ll break down the process into digestible steps, ensuring you’re equipped to conquer any network challenge. Think of it as a roadmap to network nirvana.
Installation and Setup
To get started, you need the WinCap software. Download the latest version from the official website. Follow the on-screen instructions, ensuring you have the right permissions. Once installed, launch the application. The user interface should be intuitive enough to navigate. Proper installation is the cornerstone of successful network analysis.
Capturing Network Data
This is where the real fun begins. Choose the network interface you want to monitor. Define the capture filter, specifying the protocols and data you’re interested in. Configure the capture length and save the data in a format suitable for analysis. The key here is selecting the right parameters for a focused capture.
Analyzing Captured Data
With the data in hand, you can start dissecting the network traffic. WinCap provides tools to decode packets, revealing their contents and source. Visualize the data in graphs and charts for easier comprehension. A deep understanding of the captured data is crucial for network troubleshooting.
Data Interpretation
Now comes the interpretation part. Identify patterns and anomalies in the captured data. Correlate this information with your network configuration and known issues. Compare the captured traffic with expected traffic to identify any discrepancies. Think of it as deciphering a complex code. This crucial step will help you understand what’s happening on your network.
| Step | Action | Description | Example |
|---|---|---|---|
| Step 1 | Download and install WinCap | Obtain the necessary software and install it on your system. | Download the latest WinCap version from the official website. |
| Step 2 | Select the network interface | Choose the network adapter you want to monitor. | Select the Ethernet adapter for your local network. |
| Step 3 | Configure capture filter | Specify the protocols and data to capture. | Filter for HTTP traffic to analyze web browsing activity. |
| Step 4 | Start capture | Initiate the data collection process. | Click the “Start Capture” button in WinCap. |
| Step 5 | Stop capture | End the data capture session. | Click the “Stop Capture” button. |
| Step 6 | Analyze captured data | Examine the collected data to identify patterns. | Look for unusual network traffic or errors in the captured data. |
| Step 7 | Interpret data | Draw conclusions based on the analysis. | Determine if the network issue is due to a specific application or device. |
Relevant Technologies and Tools

Wincap, like any serious digital detective tool, relies on a suite of powerful technologies and tools. Think of it as a digital toolbox, each tool designed for a specific task. Understanding these tools is key to maximizing Wincap’s potential and leveraging its capabilities effectively.
Networking Protocols
Wincap operates within the digital realm, primarily interacting with network protocols. These protocols are the unspoken language of the internet, dictating how data flows between computers. Knowing these protocols is like knowing the secret handshake of the digital world. Understanding TCP/IP, UDP, and other relevant protocols is critical to effectively interpreting and analyzing network traffic. These protocols define how data is packaged, addressed, and transmitted across networks, enabling Wincap to capture and dissect the information. This detailed understanding allows Wincap to filter, analyze, and present data relevant to its specific functions.
Packet Capture Libraries
Capturing network packets is the core function of Wincap. This requires specialized libraries that can interface with network interfaces to collect raw data. Think of these libraries as the eyes and ears of Wincap, allowing it to see and hear the data flowing across the network. These libraries are essential for intercepting and recording network traffic, forming the bedrock of Wincap’s functionality. The efficiency and reliability of these libraries directly influence Wincap’s ability to process and analyze the vast amount of data it collects. High-performance packet capture libraries are essential for Wincap to function smoothly.
Data Analysis Tools
Wincap isn’t just about collecting data; it’s about extracting meaningful insights from it. This requires specialized tools for analyzing the captured packets. These tools provide the ability to dissect the data, identify patterns, and understand the context of the interactions. Think of them as the digital magnifying glasses that allow Wincap to examine the intricate details of network communication. Data analysis tools allow for the identification of malicious activities, security breaches, and other critical information. For instance, Wireshark, a popular network protocol analyzer, is frequently used in conjunction with Wincap to perform in-depth analysis of captured packets.
Operating System APIs
Wincap interacts with the underlying operating system to access network interfaces and other necessary resources. This interaction relies on the operating system’s Application Programming Interfaces (APIs). These APIs act as the intermediaries between Wincap and the operating system, enabling Wincap to utilize the system’s capabilities. This interaction ensures that Wincap can function seamlessly within the operating system environment, facilitating the capture and analysis of network traffic. Without proper access to operating system APIs, Wincap would be severely limited in its functionality.
Programming Languages
Programming languages, like C++, are the fundamental building blocks for developing Wincap. These languages provide the structure and logic necessary for creating the software. They are the language in which Wincap’s core functionalities are defined and implemented. This allows for the development of sophisticated filtering and analysis mechanisms, creating a robust and powerful tool for network traffic analysis. Without programming languages, Wincap wouldn’t exist.
Illustrative Examples of Wincap
Wincap, the ultimate network sniffing tool, is like having X-ray vision for your network traffic. It lets you see what’s happening under the hood, from encrypted packets to simple chat messages. Imagine uncovering hidden secrets in the digital world – that’s the power of Wincap. Let’s dive into some real-world examples.
Understanding the context of each example is crucial to appreciating Wincap’s versatility. Each scenario highlights a different use case, demonstrating how Wincap can be employed for both benign and potentially malicious purposes. Ethical use of Wincap is paramount, and we’ll emphasize these principles throughout the examples.
Network Intrusion Detection
Wincap’s ability to capture and analyze network traffic is a cornerstone of intrusion detection systems. For example, imagine a network administrator using Wincap to monitor traffic patterns. They might observe unusual spikes in traffic originating from a specific IP address. This could indicate a potential intrusion, allowing the administrator to investigate further and potentially block malicious activity. Wincap can identify the source and type of malicious packets, helping prevent significant damage.
Security Audits
Wincap can be a powerful tool during security audits. Consider a company performing a vulnerability assessment on their network. Using Wincap, they can capture and analyze network traffic during normal operation. This analysis can reveal weak points in their security protocols, like unencrypted passwords or vulnerable services. This allows the company to proactively address these vulnerabilities before they are exploited by malicious actors.
Forensics Analysis
In a scenario involving a suspected cyberattack, Wincap can be a vital tool for forensic analysis. Imagine law enforcement investigators needing to understand the sequence of events during a suspected intrusion. Wincap can capture network traffic leading up to and following the suspected attack. This data can reveal crucial information about the attackers’ methods, tools, and the extent of the damage. The detailed logs and captured packets help trace the attack path and identify the perpetrators.
Example Use Case: Monitoring Web Traffic
Diagram Description: This diagram illustrates Wincap in action. A stylized representation of a computer network is shown, with several devices connected, including a web server (labeled with a stylized web icon) and a client machine (labeled with a user icon). Wincap is depicted as a central monitoring tool (labeled “Wincap”) connecting to the network. The diagram displays various data streams between the web server and the client. Thick arrows signify high-volume data transfers, and thin arrows depict smaller data streams. The labels on the arrows represent data types, such as HTTP requests and responses. The Wincap window is depicted displaying the captured packets, with columns for timestamps, source IP, destination IP, and protocol type. This graphic demonstrates Wincap’s ability to monitor and capture various types of web traffic.
Final Wrap-Up
In conclusion, wincap emerges as a versatile tool with substantial applications across a wide spectrum of disciplines. This comprehensive analysis provides a thorough understanding of wincap’s diverse facets, from its foundational principles to its practical implementation. The exploration of wincap’s types, applications, and associated technologies offers a detailed insight into its capabilities and limitations.





