Windows Defender Security Center is your essential shield against evolving cyber threats. This comprehensive guide delves into its core functionalities, helping you understand and effectively utilize its robust security features. From identifying common threats to troubleshooting potential issues, this resource empowers you to navigate the digital landscape with confidence.
This guide will walk you through the key features, configuration options, and troubleshooting steps for the Windows Defender Security Center. Understanding how to effectively manage security threats is paramount, and this guide is your key to maximizing the potential of this built-in security solution.
Troubleshooting Security Center Issues
Windows Defender Security Center, while generally reliable, can encounter occasional issues. Understanding potential problems and their solutions is crucial for maintaining a secure system. This section details common problems, their causes, and effective troubleshooting steps.
Troubleshooting Security Center issues involves a systematic approach. First, ascertain the specific problem being encountered. Is it a false positive alert? A scan error? Difficulties with real-time protection? Identifying the precise issue guides the subsequent troubleshooting steps.
Common Security Center Problems and Solutions
Troubleshooting begins with identifying the specific issue. Is the Security Center displaying unexpected alerts? Are scans failing? Or is real-time protection not functioning correctly? Pinpointing the issue helps target the solution effectively.
- False Positive Alerts: Security Center can sometimes flag legitimate files or activities as threats. This often stems from misinterpretations of file signatures or contextual analysis. A common cause is software updates or newly installed applications that are not yet fully recognized by the system’s threat detection database. Users should verify the flagged item’s reputation using reputable online security resources and consider adding the legitimate file to an exclusion list if appropriate. This avoids unnecessary disruption to normal operations.
- Real-Time Protection Issues: Real-time protection may fail to function properly due to conflicting software, insufficient system resources, or incorrect configuration settings. Ensure that no other security software is interfering with Windows Defender’s real-time protection. Insufficient system resources, such as low RAM or CPU performance, can hinder real-time protection. Review system resources and optimize them if necessary. Verify that Windows Defender’s real-time protection service is running and has the necessary permissions.
- Scan Errors: Scan errors can arise from various causes, including insufficient disk space, corrupted system files, or outdated virus definitions. Insufficient disk space can prevent a scan from completing. Free up sufficient space on the system drive or on any other partitions involved in the scan process. Verify that the virus definition database is up-to-date. Run the Windows Update utility to ensure the latest updates are installed. Check for system file integrity using the System File Checker tool.
Resolving Scan Errors
Scanning issues can often be resolved by addressing underlying system conditions or updating critical components. Regular maintenance and proactive measures prevent many scan errors.
- Insufficient Disk Space: A full hard drive can hinder scan processes. Free up sufficient space on the system drive or any other partitions involved in the scan process. Delete unnecessary files, move files to external storage, or defragment the hard drive.
- Corrupted System Files: Corrupted system files can disrupt the scanning process. Run the System File Checker tool to repair any damaged files. The System File Checker tool helps restore damaged system files to their original, functional state. Follow the prompts to identify and replace corrupted system files.
- Outdated Virus Definitions: Outdated virus definitions can lead to incomplete scans or incorrect results. Ensure the virus definition database is up-to-date. Check the Windows Update utility to ensure the latest updates are installed.
Contacting Support
If troubleshooting steps fail to resolve the issue, contacting Windows Defender support or utilizing online resources can provide further assistance.
- Online Support Resources: Microsoft provides extensive online documentation, forums, and support communities. These resources often offer detailed information and solutions to common issues. Consult the official Microsoft documentation for comprehensive guidance on Windows Defender Security Center.
- Technical Support: For more complex or persistent problems, contacting Microsoft support channels is an option. Microsoft support personnel can provide tailored assistance for resolving issues that cannot be addressed through self-help methods. Seek professional assistance for complex and unresolved problems.
Advanced Features and Tools
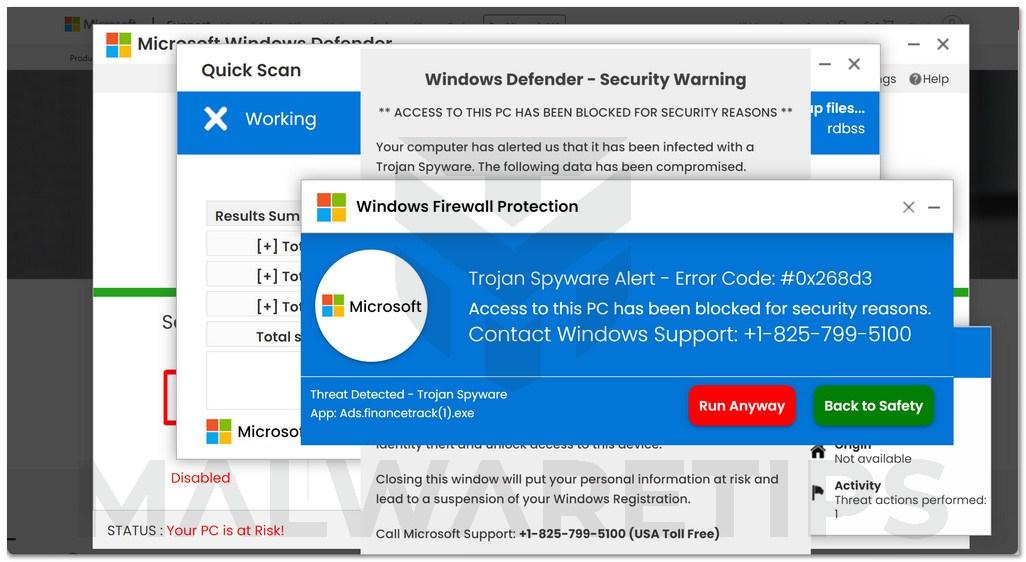
Windows Defender Security Center, while providing comprehensive real-time protection, offers advanced features for users seeking granular control and proactive security management. These features empower users to tailor their security posture to specific needs, extending beyond basic threat detection to proactive risk mitigation. Understanding and leveraging these tools can significantly enhance the overall security of a system.
Advanced features within the Security Center allow users to customize security rules, configure advanced threat protection, and gain insights into system security health. This granular control enables users to respond effectively to emerging threats and optimize their security posture.
Custom Security Rules
Custom security rules provide a means to tailor threat protection to specific organizational or individual needs. These rules go beyond the default protections offered by Windows Defender, enabling users to define their own criteria for identifying and responding to threats. By creating custom rules, users can more precisely manage security policies.
- Defining the scope of the rule is crucial. This includes specifying the types of files, processes, or network connections that the rule will monitor. Clear definitions minimize false positives and ensure the rule’s impact is targeted.
- Rules can be designed to block specific actions, such as file execution or network connections to particular IP addresses. These rules can be designed to block or allow specific behavior.
- Defining conditions is another critical aspect of creating a custom rule. This involves specifying the criteria that must be met for the rule to trigger. Conditions can be based on file types, process names, network ports, or user accounts.
- Actions are the responses triggered when the rule’s conditions are met. Actions can include blocking the action, logging the event, or taking other pre-defined steps.
Creating Custom Security Rules
Creating custom security rules within Windows Defender Security Center involves several steps. This process allows users to adapt their security posture to their unique environment.
- Open the Windows Defender Security Center.
- Navigate to the “Virus & threat protection” section.
- Select “Virus & threat protection settings.”
- Click on “Manage settings.”
- In the “Manage settings” window, find the “Custom rules” section and select “Create a rule.”
- Specify the rule’s conditions and actions, ensuring the rule aligns with desired security objectives.
- After defining the conditions, review and finalize the rule’s settings.
- Select “Create” to save the rule.
Importance of Keeping Windows Defender Security Center Updated
Regular updates to the Windows Defender Security Center are essential for maintaining effective security. These updates incorporate the latest threat intelligence, enhancing the protection against evolving threats.
- Updates provide enhanced detection capabilities for newly emerging threats.
- Regular updates ensure the software’s compatibility with new malware types and attack vectors.
- Updates address vulnerabilities in existing security components, significantly bolstering the system’s defenses against attacks.
Security Center Integration with Other Windows Components
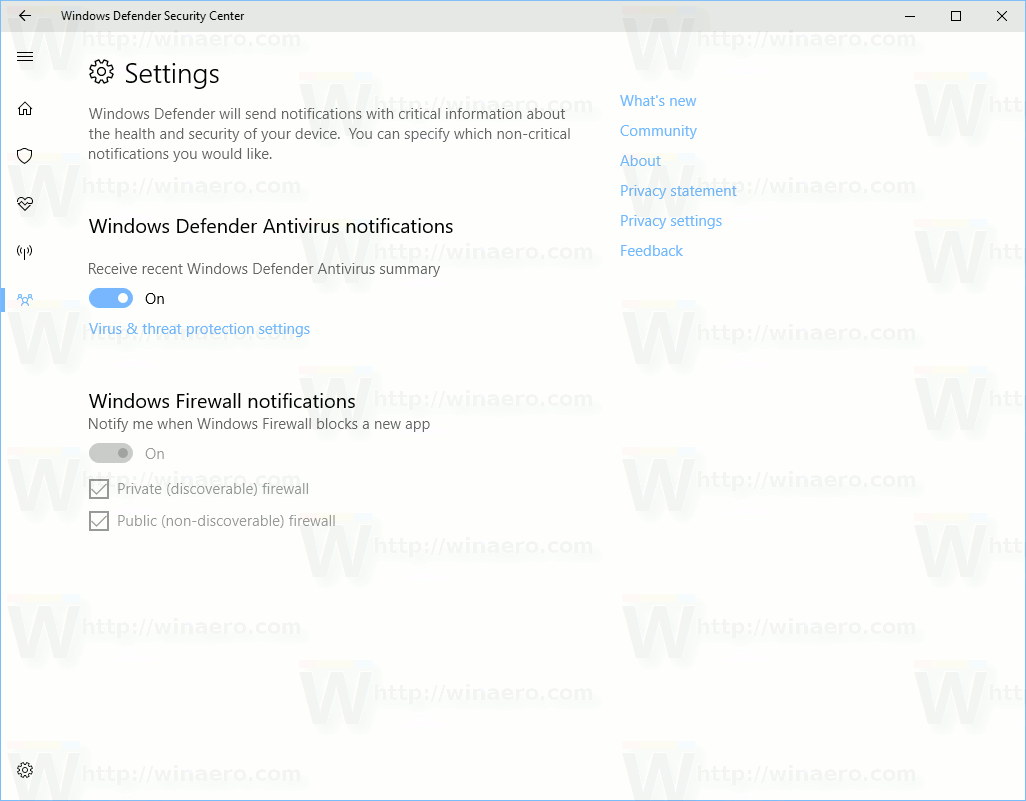
Windows Defender Security Center acts as a central hub for managing various security aspects of the Windows operating system. Its integration with other core components like Windows Firewall, Windows Update, and potentially other security-related features, provides a cohesive and streamlined security management experience for users. This holistic approach ensures that security measures are consistently applied and coordinated across the system.
The integration process between Windows Defender Security Center and other components involves a complex interplay of APIs, services, and data sharing. This seamless integration allows for real-time monitoring and proactive threat response. Security Center constantly gathers information from various sources, processes it, and presents actionable insights to the user. This dynamic interaction between Security Center and other components allows for a comprehensive view of the system’s security posture.
Windows Firewall Integration
Security Center leverages the capabilities of Windows Firewall to enforce network security policies. It monitors and controls network traffic, ensuring that only authorized connections are permitted. Security Center provides a user-friendly interface for configuring firewall rules, thereby offering granular control over network access. This interaction enables a layered approach to security, combining the broad-spectrum protection of Security Center with the detailed network control offered by Windows Firewall.
Windows Update Integration
Security Center integrates with Windows Update to ensure that the system is consistently updated with the latest security patches and improvements. This integration is crucial for maintaining the system’s security posture against emerging threats. Security Center monitors update status and notifies users of pending security updates. This proactive approach minimizes vulnerabilities and strengthens the system’s overall defense against threats. By integrating with Windows Update, Security Center ensures the user has the latest defenses available.
Integration with Other Features
Security Center’s integration extends beyond Windows Firewall and Windows Update. It can potentially interact with other features, such as the built-in antivirus engine, to provide a holistic view of the system’s security posture. This integrated approach allows for better threat detection and response, ensuring a comprehensive security strategy. The precise nature of these integrations can vary based on the specific version of Windows and the included security features.
| Feature | Interaction with Security Center |
|---|---|
| Windows Firewall | Security Center monitors and manages firewall rules, providing a centralized view of network access controls. It allows users to configure firewall rules through a user-friendly interface. |
| Windows Update | Security Center proactively monitors update status and notifies users of available security updates. This ensures that the system is protected against known vulnerabilities by installing the latest patches. |
| Antivirus Engine | Security Center integrates with the built-in antivirus engine to provide a comprehensive security solution. It leverages real-time threat detection and response capabilities to maintain system integrity. The precise level of integration may vary depending on the specific implementation. |
Final Summary
In conclusion, Windows Defender Security Center provides a powerful and integrated security solution for Windows users. By understanding its features, configurations, and troubleshooting procedures, you can confidently enhance your system’s protection against various cyber threats. This guide equips you with the knowledge to effectively use this built-in security tool, optimizing your digital experience and minimizing potential risks.