Navigating the complexities of Xero login is crucial for seamless business operations. This comprehensive guide delves into every facet of the process, from the initial login steps to advanced security protocols and troubleshooting common issues. Whether you’re a seasoned Xero user or new to the platform, this resource provides a detailed overview, ensuring a secure and efficient experience.
From understanding the diverse user roles and their corresponding access levels to exploring alternative access methods and mobile app integration, this guide covers it all. This in-depth look at Xero login empowers users to optimize their workflow and maintain the highest security standards.
Xero Login Process
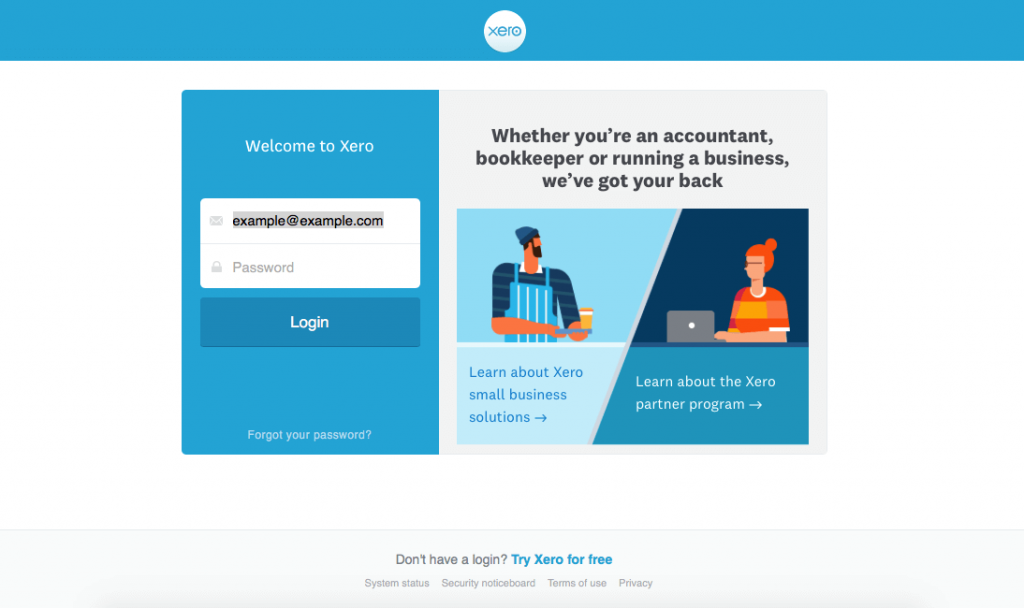
The Xero login process is a fundamental aspect of accessing and utilizing the accounting software. A smooth and secure login experience is crucial for efficient financial management. Understanding the steps involved and potential issues can significantly improve the user experience.
Xero Login Procedure
This section Artikels the standard steps for logging into a Xero account. Different login methods provide flexibility, and each method presents a specific user interface.
- Email Login: Users typically enter their registered Xero email address and password in designated fields. The email address serves as a unique identifier, ensuring proper account access. The password safeguards sensitive information, protecting the account from unauthorized access.
- Username Login: Some accounts utilize a username instead of or in addition to an email address. The username is often a unique alphanumeric identifier, chosen by the user during account setup. The user should input their username and corresponding password to log in.
User Interface Elements
During the login process, users encounter specific interface elements. These elements guide the user through the process.
- Fields: The login page usually contains fields for entering the email address (or username) and password. These fields are clearly marked, allowing users to easily input their credentials.
- Buttons: A prominent “Login” button is typically visible, allowing users to initiate the login process after inputting their credentials. Other buttons, such as “Forgot Password,” may also be present.
- Error Messages: If login attempts are unsuccessful, Xero displays error messages to guide users. These messages typically indicate the reason for the failed login, such as incorrect credentials or account suspension. For example, if a user enters an incorrect email or password, the system will display a message stating “Invalid credentials.”
Common Login Errors and Solutions
The following table lists typical login errors and their corresponding solutions.
| Error | Solution |
|---|---|
| Incorrect email address or password | Double-check the entered email address and password for accuracy. If unsure, reset the password or request a password reset. |
| Account locked | Contact Xero support for assistance. This might occur due to multiple failed login attempts. |
| Account suspended | Contact Xero support for further guidance. There might be issues with the account’s status or compliance with terms of service. |
| Network connection issues | Verify the internet connection. If the connection is unstable, try logging in again after ensuring a stable internet connection. |
Password Recovery
If a user forgets their password, Xero provides a recovery mechanism. The process varies slightly depending on the specific account details.
- Via Email: Often, users can reset their password by clicking a “Forgot Password” link. This initiates a password reset process where a unique link is sent to the registered email address. The link allows users to create a new password.
Xero Login Security
Xero’s commitment to safeguarding user data is paramount, a testament to their dedication to maintaining the integrity of their platform. Robust security measures are crucial for the confidence of all users. This section delves into the specific security protocols employed by Xero to protect user accounts, while also highlighting potential vulnerabilities and practical steps for enhancing login security.
Xero utilizes a multi-layered approach to account protection, combining advanced technologies and best practices. This strategy is designed to thwart malicious attempts and maintain a secure environment for financial transactions. A critical aspect of this security framework is the proactive identification and mitigation of potential risks.
Security Measures Employed by Xero
Xero employs a comprehensive suite of security measures, including two-factor authentication (2FA), strong password policies, and regular security audits. These measures are designed to protect user data and prevent unauthorized access. The implementation of encryption protocols during data transmission is a fundamental aspect of this security framework.
Potential Security Risks
Phishing scams, impersonation, and malware attacks are potential risks associated with Xero logins. Users must remain vigilant against fraudulent attempts to gain access to accounts. The threat landscape evolves constantly, and staying informed about current tactics is essential. Phishing attempts often mimic legitimate Xero communications, employing deceptive tactics to trick users into revealing sensitive information.
Enhancing Xero Login Security
Users can bolster their security posture by employing strong passwords, enabling 2FA, and regularly reviewing account settings. Furthermore, users should avoid clicking suspicious links or downloading attachments from unknown sources. This proactive approach minimizes the risk of falling victim to phishing attacks.
Comparison of Security Protocols
Different login methods, such as password-based login and 2FA, employ distinct security protocols. Password-based login relies solely on the strength of the password, which is susceptible to brute-force attacks. 2FA adds an extra layer of security by requiring a second verification step, typically via a mobile device or authenticator app. This two-step verification significantly enhances the security posture. This table Artikels the comparative security strengths:
| Login Method | Security Protocol | Vulnerability | Enhanced Security |
|---|---|---|---|
| Password-based | Password complexity | Brute-force attacks, dictionary attacks | Strong passwords, password managers |
| Two-Factor Authentication (2FA) | Combination of password and one-time code | Compromised device | Strong passwords, authenticator apps, device security |
Strong passwords, using a combination of uppercase and lowercase letters, numbers, and symbols, significantly enhance account security. Password managers can assist in generating and storing complex passwords, further bolstering security.
Xero Login Issues
Navigating the digital realm of business management can sometimes present unforeseen challenges. One such common hurdle is encountering issues during the Xero login process. Understanding these potential problems and their resolutions is crucial for seamless operations. This section delves into frequent login problems and provides effective troubleshooting strategies.
Xero login difficulties, while frustrating, are often resolvable with careful attention to detail. This guide provides practical steps to address common issues, from verifying credentials to assessing network connectivity and browser compatibility. By following these Artikeld procedures, users can quickly restore access to their Xero accounts and resume their business activities.
Common Login Problems
Troubleshooting login issues often starts with identifying the root cause. Various factors can contribute to login problems, ranging from simple errors to more complex technical glitches. Understanding the potential causes empowers users to implement the appropriate solutions.
Incorrect Credentials
Incorrect username or password entries are among the most frequent login problems. Users should double-check the entered information, ensuring accuracy and attention to case sensitivity. Passwords should be strong and unique to prevent unauthorized access. If doubts persist, users should consult the previously stored passwords or contact their account manager for assistance.
Network Connectivity Problems
Network interruptions or poor internet connection can impede the Xero login process. Check your internet connection; if the connection is unstable, try a different network. Using a wired connection, if available, may improve the connection stability. Consider contacting your internet service provider for technical assistance if the issue persists.
Browser Compatibility Issues
Certain browsers may not be fully compatible with Xero’s login platform, potentially causing login problems. Xero recommends using supported browsers for optimal performance and security. If using an unsupported browser, switching to a compatible browser like Google Chrome, Mozilla Firefox, or Microsoft Edge, may resolve the issue. Updating the browser to the latest version can also enhance compatibility.
Troubleshooting Guide
| Problem | Troubleshooting Steps |
|——————————-|————————————————————————————————————————————————————————————————————————–|
| Incorrect Credentials | Verify username and password. Check for typos. Ensure case sensitivity. Use strong and unique passwords. Contact account manager if needed. |
| Network Connectivity Issues | Check internet connection. Try using a different network (e.g., Wi-Fi to Ethernet). Contact internet service provider if issue persists. Ensure the firewall isn’t blocking Xero. |
| Browser Compatibility Issues | Verify supported browsers. Update the browser to the latest version. Try a different compatible browser. Check for browser extensions that may interfere with Xero login. |
| Unable to Access the Website | Verify Xero server status. Check your internet connection, try using a different network. Try clearing your browser’s cache and cookies. If problems persist, contact Xero support. |
Contacting Xero Support
When troubleshooting efforts fail to resolve login issues, contacting Xero support is a crucial next step. Providing specific details about the problem, including error messages (if any), the operating system, and the browser used, can significantly aid the support team in identifying and resolving the issue. Maintaining a clear and concise communication style will also improve the efficiency of the support process. Xero’s support channels, such as phone support or online ticketing systems, should be readily available to facilitate the process.
Xero Login Alternatives
Accessing Xero data extends beyond the traditional login method. Alternative pathways offer flexibility and enhanced integration with existing business systems, crucial for streamlined operations in the modern Maluku business landscape. This section explores diverse approaches to accessing Xero data, highlighting their features, limitations, and integration possibilities.
Alternative Access Methods
Different methods provide access to Xero data, bypassing the direct login process. This diverse approach offers significant benefits, particularly for businesses seeking tailored solutions.
| Access Method | Description | Features | Limitations |
|---|---|---|---|
| Xero API | A programming interface enabling automated data retrieval and manipulation. | Customizable data extraction, integration with other systems, real-time updates. | Requires technical expertise, potentially complex setup and maintenance. |
| Xero Reporting Tools | Pre-built reports offering insights into specific aspects of financial data. | Simplified data analysis, ready-made templates, tailored to common business needs. | Limited customization, may not offer the granular level of detail for complex analysis. |
| Xero Add-ons | Third-party integrations providing enhanced functionalities and integrations. | Automated data transfer, streamlined workflows, specific functionalities like inventory management. | Potential compatibility issues with existing systems, reliance on third-party support. |
Integrating Xero Data with Other Applications
Integration with other business applications significantly enhances the value of Xero data. This seamless connection facilitates a more efficient and comprehensive business management process.
- Accounting Software: Xero seamlessly integrates with various accounting packages, facilitating data transfer and reducing manual effort. This streamlines financial reporting and analysis.
- CRM Systems: Integrating Xero with CRM systems allows for better customer relationship management by connecting financial data with customer interactions. This aids in targeted marketing and sales strategies.
- Inventory Management Systems: Linking Xero to inventory management tools provides a holistic view of business operations, improving inventory control and reducing discrepancies. This allows businesses to optimize stock levels and improve efficiency.
Advantages and Disadvantages of Xero Alternatives
Choosing the right Xero alternative depends on specific business needs and technical capabilities. Each option offers unique advantages and drawbacks.
- Xero API: Provides unparalleled customization and flexibility, but requires significant technical expertise for implementation and maintenance. This allows for highly specialized data analysis and custom integrations.
- Xero Reporting Tools: Offers user-friendly access to pre-defined reports, ideal for users seeking quick insights into key financial metrics. However, this approach may limit customization and in-depth analysis capabilities.
- Xero Add-ons: Provide tailored functionality and integration with existing systems, simplifying specific workflows. However, compatibility and support from third-party providers are critical factors to consider.
Xero Login for Different User Roles

Accessing Xero’s functionalities is tailored to the specific roles of its users, enabling streamlined workflows and optimized efficiency. This granular control ensures that each user interacts with the system according to their designated responsibilities. This detailed look into Xero’s user roles clarifies the distinct permissions and restrictions for each.
User Role Differentiation in Xero
Xero’s robust system distinguishes user roles, each with unique access levels. This stratification ensures that sensitive financial data remains secure while empowering each user to perform their designated tasks efficiently. The various roles determine the level of control and visibility each user has within the Xero platform.
Administrator Role
The Administrator role holds the highest level of access within Xero. This role is responsible for overseeing all aspects of the Xero account. They have complete control over user accounts, settings, and financial data. This includes the ability to add, modify, and remove other users, manage bank accounts, and configure system settings. Their access grants them the authority to make crucial decisions regarding the Xero account’s operations.
Accountant Role
Accountants in Xero possess a significant level of access, but are restricted from some administrative tasks. They are typically granted the authority to manage financial transactions, including recording invoices, expenses, and payments. Their role focuses on day-to-day financial management, reporting, and analysis within the platform. They can usually view and modify financial data within their designated permissions.
Employee Role
Employees within Xero have a limited set of permissions, primarily focused on tasks related to their specific responsibilities. This includes tasks such as creating and managing invoices, expenses, and payments, depending on the configuration and assigned permissions by the Administrator or Accountant. They are typically restricted from administrative tasks, ensuring that sensitive data remains secure.
Permissions and Restrictions Table
| User Role | Access to Financial Data | Access to User Management | Access to System Settings | Specific Permissions |
|---|---|---|---|---|
| Administrator | Full Access | Full Access | Full Access | Manage all aspects of the account, including adding/removing users, modifying settings, and configuring system access. |
| Accountant | Full Access (within their permissions) | Limited Access (usually only to their own account access) | Limited Access (usually only to their own account access) | Manage financial transactions, generate reports, and perform analysis. |
| Employee | Limited Access (based on designated tasks) | No Access | No Access | Perform specific tasks related to their roles, such as creating invoices or expenses, within the confines of their permissions. |
Xero Login and Mobile Devices
Accessing Xero’s robust accounting platform from mobile devices has become increasingly prevalent. This seamless integration allows users to manage their finances on the go, fostering greater flexibility and efficiency in their daily operations. The Xero mobile app offers a user-friendly interface, enabling quick access to crucial financial data and tools, regardless of location.
Xero Mobile App Login Process
The Xero mobile app login process mirrors the desktop experience, prioritizing security and user convenience. Users typically input their existing Xero credentials – username and password – to initiate the login. Successful authentication unlocks access to a streamlined dashboard displaying key financial metrics and actionable insights. The app utilizes secure protocols to protect sensitive data during the login procedure.
Advantages of Mobile Login
Utilizing Xero through mobile devices presents numerous benefits. Users gain greater flexibility, enabling them to manage finances anytime, anywhere. This real-time access streamlines workflow and decision-making. Mobile login facilitates quick access to critical financial reports and data, crucial for informed business decisions. Furthermore, the mobile app’s design often incorporates intuitive navigation, making it easy to find and utilize essential features.
Disadvantages of Mobile Login
While mobile access to Xero offers considerable advantages, certain limitations exist. The reliability of mobile login depends on consistent internet connectivity. Interruptions or slow internet speeds can hinder access to critical information and applications. The mobile interface, while user-friendly, might not offer the same level of customization or functionality compared to the desktop version. Furthermore, data security on personal mobile devices is a concern, and users must take appropriate measures to safeguard their login credentials.
Comparison of Xero Login Experiences on Different Mobile Platforms
The Xero mobile app’s performance varies across different operating systems. On iOS devices, the app often exhibits a smoother user experience, with intuitive navigation and seamless integration with other Apple ecosystem apps. Android users might encounter minor differences in the app’s design and functionality. Differences in platform features and user interface designs can lead to slight variations in user experience. However, the core functionalities and security measures are generally consistent across both platforms.
Security Considerations for Xero Mobile Logins
Security is paramount when using mobile devices to access Xero. Users should employ robust password practices, utilizing unique and complex passwords for their Xero accounts. Activating two-factor authentication (2FA) significantly enhances security by adding an extra layer of protection. Regularly updating the Xero mobile app ensures that the latest security patches are implemented. Furthermore, users should be cautious about public Wi-Fi networks when logging in to Xero from mobile devices.
Xero Login and Third-Party Integrations
In today’s interconnected business world, seamless integration with various applications is paramount. Xero, a powerful accounting platform, recognizes this need and provides avenues for third-party integrations. These integrations allow businesses to connect Xero with other essential tools, streamlining workflows and enhancing overall efficiency.
Third-party applications leverage Xero’s Application Programming Interface (API) to access and interact with Xero account data. This allows for automated data transfer, report generation, and customized workflows, significantly boosting productivity. Understanding these integrations and their security implications is vital for businesses utilizing Xero.
Interaction with Xero Logins
Third-party applications connect to Xero through a secure authentication process. Users authorize these applications to access specific Xero data, defining the scope of the interaction. This authorization typically involves a two-factor authentication process for enhanced security, protecting sensitive financial information.
Popular Third-Party Integrations
Several popular third-party applications integrate with Xero, offering diverse functionalities. These include tools for inventory management, customer relationship management (CRM), and project management.
- Inventory Management Tools: These integrations facilitate automated inventory tracking, order processing, and reporting, directly linked to Xero’s financial data. This eliminates manual data entry and ensures accuracy in inventory valuation and cost calculations. Real-time updates of inventory levels directly reflect in financial reports within Xero.
- CRM Systems: These systems integrate with Xero to synchronize customer data, enabling efficient management of sales leads, customer interactions, and invoice generation. This allows businesses to connect customer information directly with their financial transactions in Xero.
- Project Management Software: Integrating project management tools with Xero allows for tracking project costs, revenue, and expenses. This offers a centralized view of project financials within Xero, enabling better project budgeting and financial control.
Security Considerations
Security is paramount when utilizing third-party integrations. Businesses must carefully vet and select applications, ensuring robust security measures are in place. The level of access granted to third-party applications should be carefully considered to minimize risks. Furthermore, adhering to Xero’s security guidelines is critical to safeguard financial data.
Configuring Third-Party Integrations
The configuration process for third-party integrations varies depending on the application. Generally, the process involves authorization, setting data access permissions, and configuring data mapping.
- Authorization: The user authenticates with Xero, granting the third-party application specific access rights to Xero data. This usually involves a secure login process, often utilizing OAuth 2.0.
- Data Access Permissions: The user defines the level of data access granted to the third-party application. The more comprehensive the access, the more comprehensive the integration.
- Data Mapping: The process of mapping data fields between Xero and the third-party application ensures smooth data flow and avoids discrepancies.
Illustrative Scenario for Xero Login
A common digital challenge faced by business owners is the frustration of encountering login difficulties with accounting software. This scenario illustrates a typical problem and the systematic approach to resolving it. Proper troubleshooting and account security measures are paramount to maintaining a seamless workflow.
A user, named Amelia, a sole proprietor running a small-scale bakery, experiences an issue logging into her Xero account. She has used the service for years without problems, but today she is confronted with a “Login Failed” message.
Troubleshooting Steps
Amelia first verifies her internet connection, ensuring it is stable and reliable. She then checks for any recent updates or changes to her internet service provider’s network. Subsequently, she double-checks her Xero login credentials, ensuring the correct username and password are entered, paying meticulous attention to capitalization.
Verification of Login Credentials
Amelia meticulously examines her Xero username and password, ensuring accuracy and correctness. She re-enters the credentials, checking for typos. She also verifies if the login page URL is the official Xero site and not a phishing attempt. By double-checking her input and scrutinizing the URL, Amelia ensures the authenticity of the login process.
Reviewing Xero Login History
Amelia reviews her Xero login history to identify any unusual activity or recent changes to her account settings. This enables her to spot any suspicious login attempts or account modifications that could indicate a security breach.
Contacting Xero Support
After thorough self-assessment, Amelia decides to contact Xero support for further assistance. She explains the login issue, providing details like the error message, and any relevant troubleshooting steps she has already undertaken. This proactive step ensures the issue is promptly addressed by qualified support staff.
Resolving the Login Problem
Xero support confirms the issue stems from a temporary server outage. A prompt resolution involves a brief wait, until the server is restored. Amelia is then guided to re-attempt the login after a reasonable time. This proactive resolution strategy ensures a swift restoration of access to the account.
Securing the Xero Account
Upon successful login, Amelia takes proactive measures to enhance her Xero account security. She updates her password to a strong, complex one, using a combination of uppercase and lowercase letters, numbers, and symbols. She also enables two-factor authentication for an extra layer of security. This approach ensures protection against unauthorized access.
Epilogue
In conclusion, this guide provides a thorough exploration of Xero login, equipping users with the knowledge to navigate the platform with confidence. By addressing login processes, security considerations, troubleshooting, and alternative access methods, this resource aims to simplify the Xero experience for all users, regardless of their technical expertise or specific role within the organization. Ultimately, a secure and efficient Xero login is essential for maximizing productivity and minimizing potential disruptions.